Monthly Incident Sharing (Jan 2024)
Introduction
In this monthly series, HashDit is sharing the monthly security incidents in the crypto space and what we can learn from them.
For this Jan 2024 edition, the total losses mounted up to $153 million, showing a staggering 453% increase compared to January 2023.
Top 5 DApps incidents
Orbit Chain - $81.5m
Orbit Chain is a Bridge protocol, which uses the model of locking collateral on the source chain to mint wrapped tokens on the destination chain. In this attack, the hacker was able to compromise 1 of the bridge’s vault and steal its funds. Hack tx
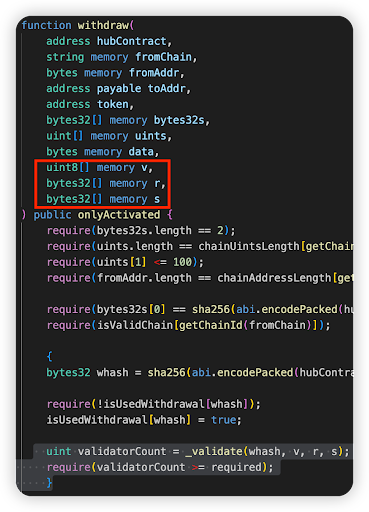
Root cause: Backend compromise. The hacker was able to produce 15 correct Signer keys (v, r, s values), although the threshold needed was just 7.
Vulnerable code snippet:
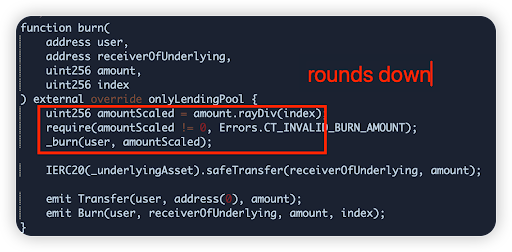
Magic Internet Money (MIM) - $6.5m
Magic Internet Money is a DeFi protocol which allows lending and borrowing of funds. In this attack, the attacker was able to compromise 1 of the protocol’s markets and steal funds. Hack tx
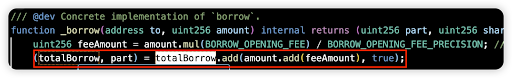
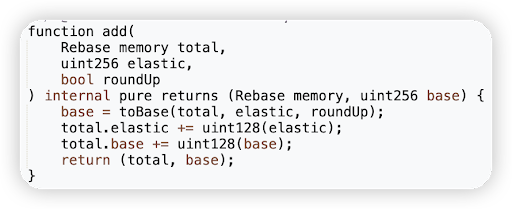
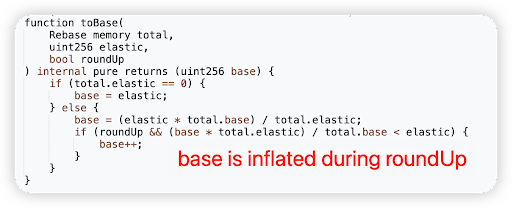
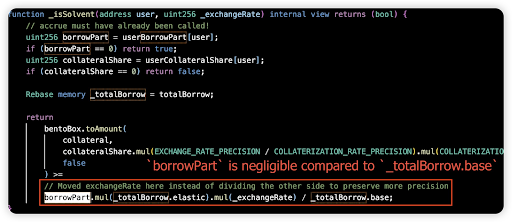
Root cause: The borrow function in CauldronV4 contracts was vulnerable to manipulation of the part parameter (the user’s share of total debt) via repeatedly borrowing and repaying an asset, taking advantage of the rounding error.
Vulnerable code snippet:
Gamma Strategies - $4.6m
Gamma Strategies is a DeFi protocol which allows active liquidity management and market making strategies. In this attack, the attacker was able to compromise 1 of the protocol’s vaults and steal funds. Hack tx
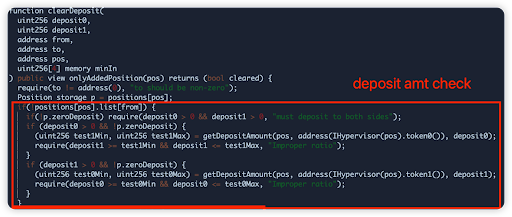
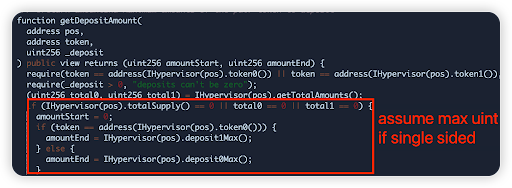
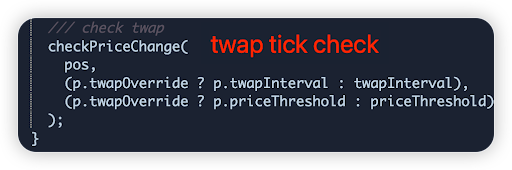
Root cause: The liquidity ratio checker function erroneously allowed for deposits in any ratio so long as the contents within the vault were single-sided. This allowed for a disproportionate amount of token 0 being deposited, gaining more shares than expected. A second issue was there was no check for the current tick to be within the base position’s lower and upper tick (only a check for the tick change)
Vulnerable code snippet:
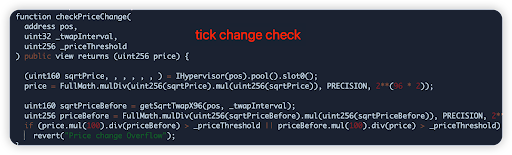
Radiant - $4.4m
Radiant is a DeFi protocol which allows lending and borrowing of funds across chains. In this attack, the attacker was able to compromise 1 of the protocol’s markets and steal funds. Hack tx
Root cause: "New/empty market" exploit. It is a known vulnerability to the combination of a rounding error and a totalSupply value of 0. Bug introduced in recent upgrade.
Vulnerable code snippet:
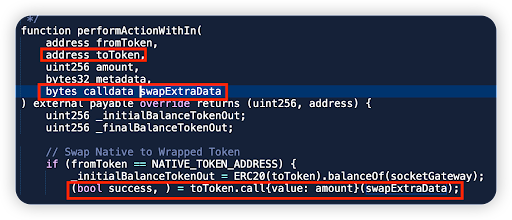
Socket Dot Tech - $3.3m
Socket Dot Tech is an Interoperability protocol bringing seamless connectivity across blockchains. In this attack, the attacker was able to compromise 1 of the protocol’s vaults and steal funds. Hack Tx
Root cause: Unsafe call in the performAction() function. The attacker constructed calldata in the swapExtraData parameter to call transferFrom() of arbitrary tokens, transferring tokens approved to the contract by other users to the attacker's address. Bug was introduced in the recent proxy upgrade.
Code snippet:
Key lessons for developers
- Keys should be properly secured, rotated regularly and have some level of decentralization. Adopt a zero-trust model. Conduct proper background checks for new employees in view of insider compromises.
- Validation is important - ensure all possible user inputs are checked for state changing methods. This is especially true for calldata parameters where attackers can craft any data and when the protocol contract handles users’ approvals.
Rounding in Solidity always rounds down. As such, it is important to perform multiplication before division and to round down for the user during withdrawals, and round up during deposits. Consider increasing precision during calculations to avoid unexpected manipulation attacks.
However, in the latest donation attacks for lending protocols, we see that the usual rule to favor protocol for calculations is no longer sufficient. There must be better health checks for bad debt as well, at the end state of a transaction.
For projects utilizing lending protocols:
- When deploying a new market (especially for Compound / Aave v2 forks), ensure that it is first initialized with 0 Collateral Factor and deploy with small deposit to lock dead shares.
- Disallow deposits when the pool price is out of the base range of liquidity.
- Increase precision on price change thresholds and deposit ratios.
- For those allowing single-sided pool deposits, add a conditional statement to prevent deposits of any ratio of assets so long as vault is single-sided.
Always engage a security auditor to review all code upgrades before they are deployed on chain. This prevents new bugs from being introduced.
Feel free to contact us at support@hashdit.io for any support needed! Stay safe!
